Course catalog
Categories
Showing 481-500 of 607 items.
R Programming in Data Science: High Variety Data
High-variety data can cause a slew of problems for data scientists. In this course, learn what these problems are and how to use the unique capabilities of R to solve them.
R Programming in Data Science: High Velocity Data
Learn how to work your mojo on high-velocity data with R. Discover how to acquire, process, and present high-velocity data using this popular programming language.
R Programming in Data Science: High Volume Data
Analyze high-volume data using R, the language optimized for big data. Learn how to produce visualizations, implement parallel processing, and integrate with SQL and Apache Spark.
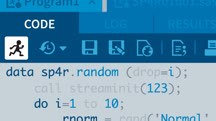
R Programming in Data Science: Setup and Start
Learn how to choose and install a version of R-base R, tidyverse R, R Open, or Bioconductor R-and install useful R packages.
R: Interactive Visualizations with htmlwidgets
Learn how to rapidly create rich, interactive data visualizations with R and htmlwidgets—packages that connect R to popular JavaScript libraries like Plotly, Leaflet, and DT.
Reasonable Cybersecurity for Business Leaders
Protect your company from cybersecurity threats, liabilities, and enforcement actions. Learn how to comply with the Federal Trade Commission's reasonable cybersecurity standard.
Reinforcement Learning Foundations
Learn the basics of reinforcement learning (RL), including the terminology, the kinds of problems you can solve with RL, and the different methods for solving those problems.
Relational Databases Essential Training
Modeling phenomena with a relational database is an invaluable skill in today’s big-data world. This course covers the fundamentals of the relational model for creating databases.
Risk Management for IT and Cybersecurity Managers
Learn about the different methods of risk management as an IT or cybersecurity manager, as well as what happens when risk management is improperly conducted.
Safeguarding AI
Make sure your organization is using artificial intelligence for good. Explore the ethical, legal, and strategic issues guiding the use of AI and machine learning.
Salesforce Administrator Cert Prep: 3 Sales, Marketing and Service Applications
Learn how to administer the sales, marketing, and service applications in the Salesforce ecosystem, as you study for the third domain of the Salesforce Certified Administrator exam.
SAS Essential Training: 1 Descriptive Analysis for Healthcare Research
Explore the fundamentals of SAS as you learn how to conduct a descriptive analysis of a health survey dataset.
SAS Essential Training: 2 Regression Analysis for Healthcare Research
Deepen your SAS knowledge by learning how to conduct a regression analysis of a health survey data center using this popular data analytics platform.
SAS Programming for R Users, Part 1
Discover how to apply your understanding of R—the language of big data—in the SAS environment.
SAS Programming for R Users, Part 2
Discover how to apply your understanding of R—the language of big data—in the SAS environment. To get the most from this course, make sure to watch part 1 of this series.
Scala Essential Training for Data Science
Use Scala in your data science work. Explore the Scala features most useful to data scientists, including custom functions, parallel processing, and programming Spark with Scala.
Securing Containers and Kubernetes Ecosystem
Learn best practices and security controls for containers and the Kubernetes ecosystem using a simple five-factor security model.
Securing Cryptocurrencies
Explore some of the basic security requirements for cryptocurrencies, as well as some tools that can help you reduce your own exposure to risk.
Securing the IoT: Introduction
Secure the Internet of Things. Explore the types of IoT devices designed to improve the quality of life in homes and businesses, discover how to design IoT security, and more.
Securing the IoT: Privacy
Explore the relationship between security, privacy, and the IoT. Learn about IoT vulnerabilities, privacy concerns, attacks and glitches, and more.